- Extensive measures have been put in place to safeguard customer data. These include and are not limited to: SSL certified web services; secure encryption at rest for sensitive Client data; and fully segregated data environments, for qualifying Customers.
- Customer Confidential data is retained only for the duration of the subscription and backed up for business continuity only.
- We are a Tier 1 registered company with the Information Commissioners Office (UK), registration ZB269898.
- Since incorporation, there have been no critical cyber issues resulting in compromised customer or client information.
- QIS Risk does not currently hold an external audit certification. As of the time of writing, we were pursuing a SOC II certifications with a target completion data in 2023.
Below is a high-level abstraction of the architectural setup for QIS Risk, briefly described here along with some of the security measures implemented at each stage. Certain details of the architecture may change, but this should provide an overview of the key security practices.
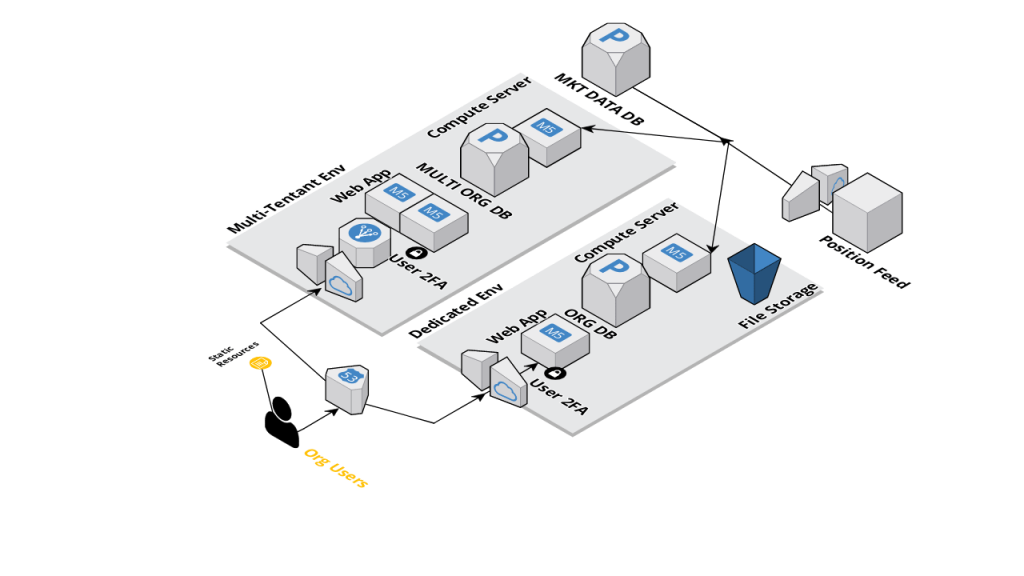
Client organization users lookup their specific QIS entrypoint on a public DNS. This will resolve their request to either a multi-tenant environment (https://app.qisrisk.com) or their own dedicated compute environment. Access to these environment is restricted using the AWS Internet Gateway which firewalls inbound traffic to only authorized ports. SSL encryption on requests is enforced at this stage.
Within the compute environment, users are authenticated at the application layer. User accounts are created by administrators and require a paper-trail request from the client contact. Passwords are SHA-256 encoded strings. All users require 2-factor authentication (2FA) which is set up as part of their first login. QIS currently supports only one-time password 2FA using RFC-6238 and our recommended client-side application is Google Authenticator.
Once authenticated, web application servers will enable users to view the organization data. This is serviced from a database instance containing organization-specific data objects (users, wallet addresses, positions, etc.). This is logically distinct from other databases in the QIS architecture, such as those containing real-time market data and estimated model parameters, with no organization-specific context. In the dedicated environments, this is a physically separate database instance for each organization. In all environments, feed-related user credentials such as read-only API keys and wallet public addresses are symmetrically encrypted using a Fernet key. Keys are rotated periodically.
Organization DBs are updated in real-time by environment-specific compute servers. These compute servers are whitelisted for access to certain resources in the network, including a market data database that's updated in real-time by another subsystem.
The compute servers also have access to outbound internet requests via an AWS Internet Gateway with appropriate firewall restrictions. These servers are identified by a short list of public IP addresses that can be used to set up restricted feed access when generating exchange read-only credentials.
Dedicated environments also allow for file storage in encrypted AWS S3 buckets. This is used, for instance, for the delivery (PULL) of files using SFTP. Credential access to these buckets is managed internally by QIS and not available to end-users.
Infrastructure and code changes are highly restricted to vetted employees. As of the time of writing, only 2 key employees were authorized to make modifications.
ENTERPRISE RISK MANAGEMENT
This policy applies to all our employees, contractors, and anyone who has permanent or temporary access to our systems and hardware.
Confidential Data
Confidential data is secret and valuable. Common examples are:
- Client account read-only authentication keys
- Account transaction data
All employees are obliged to protect this data. We give our employees instructions on how to avoid security breaches.
Personal and Company Devices
When employees use their digital devices to access company emails or accounts, they introduce security risk to our data. We advise our employees to keep both their personal and company-issued computer, tablet and cell phone secure. They can do this if they:
- Keep all devices password protected.
- Choose and upgrade a complete antivirus software.
- Ensure they do not leave their devices exposed or unattended.
- Install security updates of browsers and systems monthly or as soon as updates are available.
- Log into company accounts and systems through secure and private networks only.
We also advise our employees to avoid accessing internal systems and accounts from other people’s devices or lending their own devices to others.
When new hires receive company-issued equipment they will receive instructions for:
- Disk encryption setup
- Password management tool setup
- Installation of antivirus software
They should follow instructions to protect their devices and refer to our Security Specialists if they have any questions.
Emails
Emails often host scams and malicious software (e.g. worms.) To avoid virus infection or data theft, we instruct employees to:
- Avoid opening attachments and clicking on links when the content is not adequately explained (e.g. “watch this video, it’s amazing.”)
- Be suspicious of clickbait titles (e.g. offering prizes, advice.)
- Check email and names of people they received a message from to ensure they are legitimate.
- Look for inconsistencies or give-aways (e.g. grammar mistakes, capital letters, excessive number of exclamation marks.)
If an employee isn’t sure that an email they received is safe, they can refer to our IT Specialist.
Employee Passwords
Password leaks are dangerous since they can compromise our entire infrastructure. Not only should passwords be secure so they won’t be easily hacked, but they should also remain secret. For this reason, we advice our employees to:
- Choose passwords with at least eight characters (including capital and lower-case letters, numbers and symbols) and avoid information that can be easily guessed (e.g. birthdays.)
- Remember passwords instead of writing them down. If employees need to write their passwords, they are obliged to keep the paper or digital document confidential and destroy it when their work is done.
- Exchange credentials only when absolutely necessary. When exchanging them in-person isn’t possible, employees should prefer the phone instead of email, and only if they personally recognize the person they are talking to.
- Change their passwords every two months.
Remembering a large number of passwords can be daunting. We will purchase the services of a password management tool which generates and stores passwords. Employees are obliged to create a secure password for the tool itself, following the above mentioned advice.
Data Transfer
Transferring data introduces security risk. Employees must:
- Avoid transferring sensitive data (e.g. customer information, employee records) to other devices or accounts unless absolutely necessary. When mass transfer of such data is needed, we request employees to ask our Security Specialists for help.
- Share confidential data over the company network/ system and not over public Wi-Fi or private connection.
- Ensure that the recipients of the data are properly authorized people or organizations and have adequate security policies.
- Report scams, privacy breaches and hacking attempts
Our IT Specialists need to know about scams, breaches and malware so they can better protect our infrastructure. For this reason, we advise our employees to report perceived attacks, suspicious emails or phishing attempts as soon as possible to our specialists. Our IT Specialists must investigate promptly, resolve the issue and send a companywide alert when necessary.
Our Security Specialists are responsible for advising employees on how to detect scam emails. We encourage our employees to reach out to them with any questions or concerns.
Disciplinary Action
We expect all our employees to always follow this policy and those who cause security breaches may face disciplinary action:
- First-time, unintentional, small-scale security breach: We may issue a verbal warning and train the employee on security.
- Intentional, repeated or large scale breaches (which cause severe financial or other damage): We will invoke more severe disciplinary action up to and including termination.
We will examine each incident on a case-by-case basis.
Additionally, employees who are observed to disregard our security instructions will face progressive discipline, even if their behavior hasn’t resulted in a security breach.
INFORMATION SECURITY POLICY
Information Classification
We will only classify information which is necessary for the completion of our duties. We will also limit access to personal data to only those that need it for processing. We classify information into different categories so that we can ensure that it is protected properly and that we allocate security resources appropriately:
• Unclassified. This is information that can be made public without any implications for the company, such as information that is already in the public domain.
• Employee confidential. This includes information such as correspondence address, pay and so on.
• Company confidential. Such as contracts, source code, business plans, passwords for critical IT systems, client contact records, accounts etc.
• Client confidential. This includes personally identifiable information such as name or address, passwords to client systems, client business plans, new product information, market sensitive information etc.
The deliberate or accidental disclosure of any confidential information has the potential to harm the business. This policy is designed to minimize that risk.
Access Controls
Internally, as far as possible, we operate on a ‘need to share’ rather than a ‘need to know’ basis with respect to company confidential information. This means that our bias and intention is to share information to help people do their jobs rather than raise barriers to access needlessly.
As for client information, we operate in compliance with the GDPR ‘Right to Access’. This is the right of data subjects to obtain confirmation as to whether we are processing their data, where we are processing it and for what purpose. Further, we shall provide, upon request, a copy of their personal data, free of charge in an electronic format. We also allow data subjects to transmit their own personal data to another controller. However, in general, to protect confidential information we implement the following access controls:
• Company confidential. Accessible by company employees and third-party contractors.
• Client confidential. Accessible by company employees only on a need to know basis.
• Employee confidential. Accessible only by Company Directors via third-party administration applications.
In addition, admin privileges to company systems will be restricted to specific, authorised individuals for the proper performance of their duties.
Password Guidelines
• Change default passwords and PINs on computers, phones and all network devices
• Consider using password management software
• Don’t share your password with other people or disclose it to anyone else
• Don’t write down PINs and passwords next to computers and phones
• Use strong passwords
• Change them regularly
• Don’t use the same password for multiple critical systems
INFORMATION MANAGEMENT
Records Retention
To the best of our knowledge, we are not required to retained Client Confidential records for regulatory purposes. As such, Client Confidential data is retained only for the Subscription Term for the purpose of services provision.
Company Confidential data is backed up on multiple third-party web services as required for business continuity.
Backup for Disaster Recovery
For details on our Disaster Recovery process and associated data backups, please see this page.
